Much like the internet itself, cybercriminals seemingly never sleep. These scammers are on a never-ending quest to exploit individuals, businesses, and data for monetary gains. And one of their most pernicious forms of fraud is called smishing.
In just six months in 2021, smishing attacks spiked over 700%, costing victims over $10 billion. Victims range from individuals to businesses whose employees fall victim while using company software and communication channels. Alarmingly, the threat landscape continued to evolve in 2022, with three in four IT professionals worldwide reporting that their organization had encountered smishing attacks that year.
In this article, we’ll define smishing, explain how it works, provide a few examples, and show you how to protect yourself and your business from getting tricked by scammers.
What is smishing?
Smishing, short for SMS phishing, is an attempt to trick or manipulate individuals or businesses into revealing sensitive or valuable personal information through SMS and other forms of text messaging.
Smishers do this by impersonating real businesses (like delivery services, utility companies, financial institutions, or goverment agencies) or trusted contacts and sending fraudulent text messages to mobile phones. Exploiting trust, they trick victims into revealing personal data or business-related information, including names, dates, credit card information, financial information, social security numbers, login credentials, and passwords. They then sell that data on the black market or use it for identity theft, siphoning money from bank accounts or rerouting payments into their own pockets.
Scammers choose smishing over other types of phishing attacks for various reasons. One of the most important reasons they choose smishing is that SMS click-through rates hover around 20%, compared to email’s 3-5%. Gartner reports that SMS response rates are as high as 45%, meaning recipients are more likely to engage with an SMS than an email, which has a 6% average response rate. Additionally, scammers can mask the origins of smishing messages using tactics like spoofing or text-to-email software.
Smishing vs phishing
Smishing is a form of phishing. It refers specifically to phishing attacks that happen over SMS or other messaging channels (SMS + phishing = smishing).
Phishing attacks have been around for a long time (the first one is thought to have originated in 1995!), and they happen over a variety of communication channels and devices. Most phishing attacks have a few things in common: they typically involve deceptive tactics to trick individuals into revealing sensitive information, they often use a sense of urgency or fear to manipulate the recipient’s emotions, and frequently use websites or links that appear legitimate.
In the world of phishing, scammers present themselves as a real and legitimate business or person that the victim is likely to trust, and they use that to get them to reveal personal details that they can use to gain access to their banking information, costing the victim a lot of money and frustration.
Phishing can happen over phone (and often called “vishing”), email, social platforms, fraudulent websites, and many other channels. It can involve links to click, forms to fill out, or just talking to an actual fraudster on the phone.
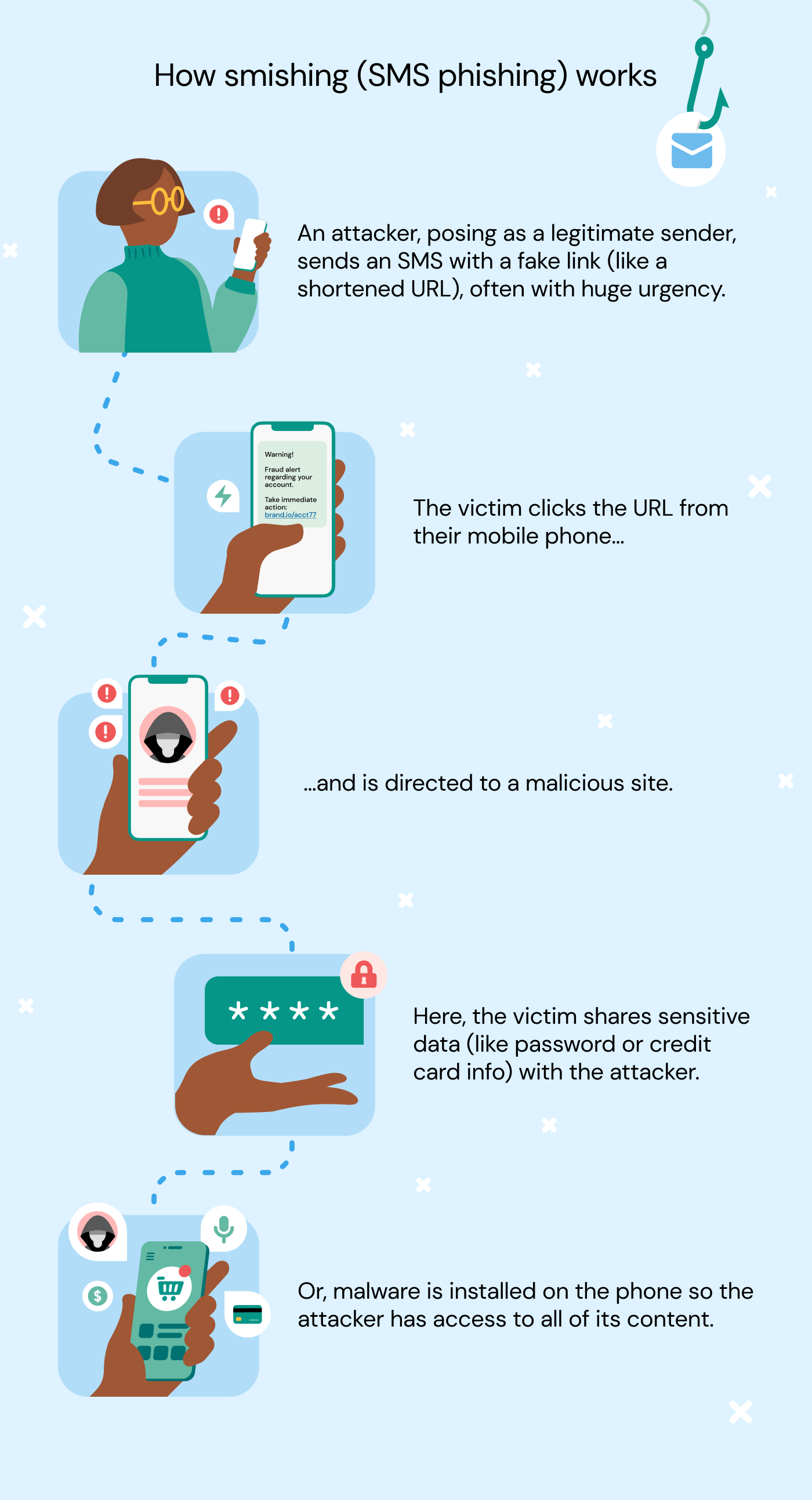
How smishing works
Smishing attacks aren’t always random, and sometimes businesses or individuals can be targeted for specific malicious intent. For smishing to work, a scammer will first need your phone number, and there are a variety of ways they can get it – data breaches are common sources, but sometimes a scammer will just guess numbers in particular area codes. In densely populated areas, they’re going to get some hits.
Once they have that, the cyberattack can commence. Here’s what happens from the victim’s perspective.
The victim receives a text message
First, the victim receives a message that appears to be from a legitimate company. It could appear to be from a bank, PayPal, Amazon, a credit card company, another company that does business with the victim’s company, a government entity, and many other sources.
Often, the phone number or other identifying information looks the same as or close enough to pass for a sender the victim trusts.
Smishing messages share common features: The message will inform the recipient that they need to click a link, fill out a form, verify their address or login information, or even call or text in order to deal with whatever situation has been invented to trick them.
Typically, these scams include some sense of urgency; there’s an important situation that requires immediate action. Sometimes, it will even tell them their account has been compromised by hackers and that they need to change their login information.
The victim clicks or responds
Next, if the victim doesn’t understand that this message is fraudulent, they may click or respond to it, thinking they need to take action now since they trust the sender.
If the message has one or more malicious links (the link itself may be the scam), clicking on it causes malware or spyware to be downloaded to their mobile device. In that case, nothing will appear to have happened. But now, an attacker has installed spyware on the victim’s smartphone and will be able to monitor their keystrokes and determine their passwords and other sensitive information. Later on, the victim may notice that a lot of money was taken from their account and wonder how they were compromised.
The victim shares sensitive information
Clicking the link included in the smishing text may also take the victim to a website that looks like it belongs to the sender, such as a bank. The page will have a form or a survey to fill out. And once they do, the fraudsters have enough information to steal or commit fraud.
The scammer uses that information to rob them
With personal information in-hand, the scammers do everything they can to ruin the victim’s life for their own benefit. The longer they have the victim’s personal data without them realizing it, the more damage the scammer can do.
Depending on what personal information the victim shared with them, the attacker may be able to steal from them immediately. Or, they may be connected to networks where they can sell private information on backchannel websites.
In that case, the victim could be scammed by multiple people before they even realize what’s happening.
What does a smishing text look like?
Smishing is just one of many types of cybercrime, but it’s one of the worst ones because of how real some of these messages appear to be. Even people who have heard of smishing scams have been known to become victims because they’re so difficult to spot.
Here are the common warning signs that a text message may be a smishing attempt:
Unusual sender number
If a well-known company sends you a text message – and you opted into receiving texts from them – any phone number they contact you with should be easy to verify. Be wary of messages originating from unfamiliar or suspicious sources, especially if they contain urgent requests, unsolicited offers, or links to click.
For example, if Amazon sends you an email saying your package couldn’t be delivered and you need to verify your address, they’re not going to give you a phone number using your local area code.
Keep note: smishers sometimes use masked sender numbers to obscure their true identities, making it crucial for you to exercise caution and verify the authenticity of any unexpected messages.
Spelling and grammar mistakes
Another hallmark of smishing scams is spelling and grammar errors. Scammers often rush their messages and struggle to put together even a few coherent sentences without making obvious grammar mistakes. However, it’s also essential to know that scammers have become increasingly proficient, using AI to generate remarkably realistic messages that look like they were written by a human.
Remember that reputable organizations and individuals usually take care to communicate clearly and professionally. Any message with misspelled words, awkward sentence structures, or language mistakes should be treated with suspicion.
URL link is shortened, obscured, or suspicious
Another way to spot smishing scams is to study the link they want you to click.
You might see extra short links that are hard to decipher, or links obscured by other graphics in the text. You may also notice an extra character thrown into a link, such as “paypall.com”. That extra ‘l’ is a dead giveaway.
Sometimes there will be extra characters elsewhere, separated by dots to make it seem more technical. For example, in the example below, you might notice that the URL is “br1ckbank.com” when the legitimate bank would be called “Brick Bank.” This illustrates the kind of small yet suspicious changes to URLs that scammers often use to trick people into clicking them.
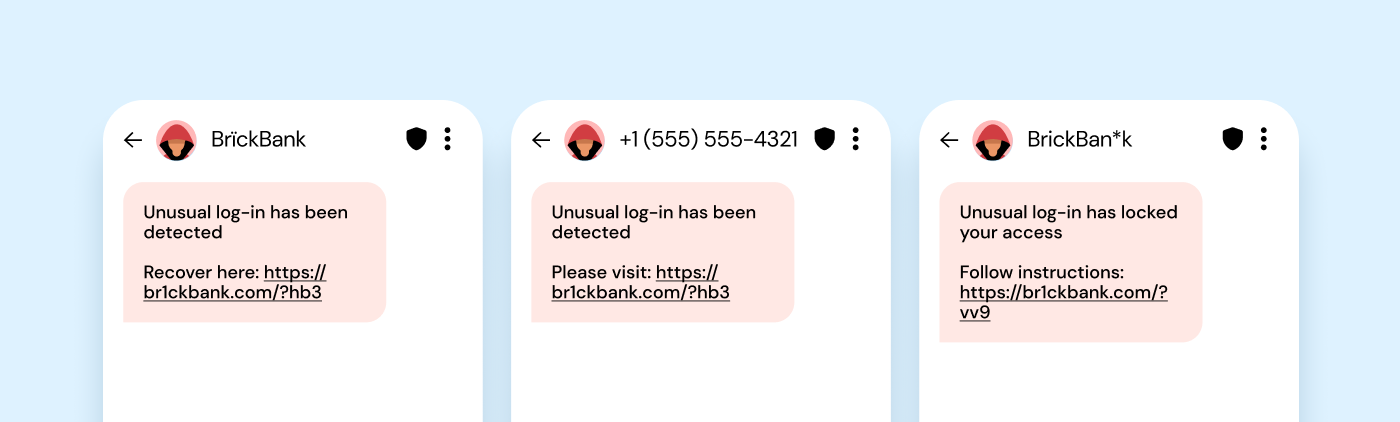
To stay safe, it’s essential to exercise caution when you receive messages of any kind that have unusual sender numbers, spelling and grammar mistakes, or suspicious URLs.
9 examples of common smishing scams
Here are some types of smishing attacks that scammers may use to deceive and defraud you under the guise of someone you trust:
1. Fake security alerts
Picture this: You get a notification that your account has been compromised and you need to re-verify your information and change your password.
It’s important to question the legitimacy of such claims. These fake security alerts are a classic smishing tactic precisely because they grab your attention. Scammers aim to deceive you into sharing your existing login credentials.
If you do end up sharing your login credentials, the scammer can now change your real password and you won’t be able to get into your own account.
2. Prize or contest scams
Everyone likes to win, so scammers prey on that desire by sending out texts that look like they’re from companies you trust announcing that you’ve won a gift card or some other contest. All you have to do is fill out a form to verify your information, and the prize will be yours.
Except there’s no prize. And once you fill out that form, the scammer has your information.
3. Shipping scams
“Your package couldn’t be delivered and we need to re-verify your address.” This is a common shipping scam message. In fact, most major carriers get impersonated by smishers regularly. Watch out for shipping scams pretending to be from UPS, FedEx, and major e-commerce retailers like Amazon.
4. Fake invoice scams
Related to the shipping scams are invoice scams. You’ll get an invoice that appears to be from a trusted source like PayPal or a reputable shipping company, claiming you owe them money.
But the invoice is fake, and if you pay it, not only do they get your money, but they have your credit card numbers and other data to extract more from your accounts. Afterwards, they may sell your information on the dark web as well.
5. Verification code requests
Unfortunately, scammers have found a way to exploit multi-factor authentication. In this scam, you’ll get a text saying you need to enter a verification code to confirm that some event has happened. It could be a money transfer, a purchase, a password change, or some other event that needs verification.
But the reality is, no genuine event happened in the first place. And once you unwittingly confirm this request, the scammers have whatever information you just gave them, potentially granting them access to your accounts and personal data.
6. Tax scams
This is a rather urgent and unsettling tactic from fraudsters who impersonate tax authorities. They might send messages saying that you owe money on your taxes, and that there will be dire consequences if you don’t settle your debts soon. However, it’s important to recognize that government agencies typically don’t operate like this, and if you do owe money, they’re not going to send you a text message. When you genuinely owe taxes, the government’s approach will be more formal – like a written letter in the mail, or other methods of communication.
On the flip side, another tax-related scheme might say that you have an unclaimed tax refund. Instead of fear, you’re motivated by the allure of a sudden cash windfall to respond.
In both cases, it’s crucial to discern that these communications aren’t from government agencies, and if you respond, you risk placing your personal information into the hands of fraudsters with malicious intent.
7. Fake financial alerts
Financial alert scams might aim to inform you about recent or impending events related to your bank or credit card accounts via SMS.
These alerts often reference different scenarios, like money transfers from or to your accounts, changes to your account, new benefits or special offers that are only available for a limited time, and that you need to do some immediate action. Make sure to stay vigilant and verify the authenticity of such messages to safeguard your financial security.
8. Texts claiming to be from someone you know
The “trusted friend” scam is a particularly difficult one to spot if you’re not paying attention. If a friend or work colleague’s information has been compromised, the scammer may be able to send you a message that really is from their phone number.
They may tell you about a family emergency they need help with, or a contest they just won, or some other message. If it doesn’t sound like something your friend or colleague would send, it’s probably because they didn’t.
You’ll learn how to deal with suspicious texts like this in the next section.
9. Sensitive information requests
This encompasses any other suspicious message via SMS. If you’re contacted via text message and are asked for sensitive data, or asked to click on a link but the explanation for why just doesn’t seem right, it’s probably a scam.
The bottom line: Very few legitimate companies will ever request sensitive information via text messages. Reputable companies are aware of the significant fraud risks associated with this and, as a result, refrain from doing it.
How to defend against SMS phishing (smishing)
Remember, as a company, there are two ways smishing can hurt you. It can hurt your individual employees, and it can hurt your entire company. It depends on the nature of the cyberattack.
If the smishing attack includes a link that uploads malware or ransomware to your company systems, the attackers could gain access to contact information of your employees and other private information.
This is one way smishers send texts that look like they are from people you know. They compromise that person’s information, and use your trust in them to try to trick you into sharing valuable personal data.
So, what can you do to prevent smishing attacks? Here are a few options.
Refrain from clicking on links from a brand or person you don’t know and trust
First, the simplest thing to do is to do nothing. If you don’t know the sender, don’t respond. Don’t click. Don’t do anything on impulse or without thinking.
Contact the sender to verify an SMS text
If the senders appear to be legitimate but you’re suspicious and don’t know how to verify it on your own, call the real company, organization, or person and verify it directly with them.
Do a web search for the scam
Some scams might include particular words, phrases, or other information that’s unique enough to search for them online. For scams that have been around a bit longer, which includes most of them since scammers aren’t creative enough to keep trying new ones every week, you may be able to find blog posts and comment threads exposing that particular scam for what it is.
So, if you can’t verify it with the company or institution, try doing a web search using information from the text itself.
Delete the SMS if you can’t verify it
If you’re pretty sure it’s a scam, just delete it. If it’s legitimate, you can be sure the company will attempt to contact you again if it’s that important.
Train your employees on smishing
Lastly, for companies, don’t leave your employees to fend for themselves. It’s essential to proactively create training programs that walk through what to look for and how to respond when they get a suspicious text message.
Emphasize the hard-to-spot smishing scams that may come from business colleagues or other companies you’ve done business with in the past.
Encourage employees to report any smishing attempts or other security concerns to the internal security team. Remember that collective awareness and swift reporting can be your organization’s first line of defense against smishing.
As a side note, you can also begin to advocate for solutions at the policy level, as smishing and other messaging scams are a global problem.
What businesses can do to prevent smishing
SMS is an amazing communication tool for businesses, offering a direct and efficient way to engage with customers and employees. However, it’s important for all of us to be wary of texts from unfamiliar companies and stay vigilant against the threat of smishing.
Here are a few key takeaways to pass on to your employees about SMS phishing:
- Verify the sender: Verify the authenticity of SMS messages, especially those requesting personal or financial information.
- Exercise caution with links/attachments: Don’t click on links from texts that you don’t recognize. Be cautious even if the message appears to be from a known contact.
- Report suspicious messages: Promptly report any messages that raise doubts or appear to be phishing attempts.
Training your employees is just one of many things businesses can do to prevent SMS phishing. This entails educating both employees and recipients about tactics employed by fraudsters, and enhancing cybersecurity measures to detect and thwart smishing and related scams like SIM farm fraud.
Check out our resources to help your business prevent fraud in business messaging. Or, learn about how Sinch SMS for operators can help you mitigate SMS fraud.



